Yesterday, Google announced yet another Security Key to be used for two-factor authentication (2FA, sometimes 2-step verification, 2SV) for Google's services. This one is built directly into Android 7+ so you may already have it in your pocket. It uses Bluetooth (but pairing isn't required) and currently works only in Chrome and Chromium-based browsers – Google says it's a beta version. And that's basically all we know about it. I use 2FA where possible, I recommend using it whenever possible so I just had to try it.
Google already has one security key – Titan. It will cost you $50, it needs to be paired (in case of the Bluetooth version) or connected to a USB port (and needs an adapter in case you only have USB-C ports) and it's just another thing to carry around. I'm pretty sure at least one of those things will discourage the majority of users from using the key. Even the maker of YubiKey authentication dongles wasn't quite happy with the Titan.

Google Titan security keys (source)
Google also supports Prompts for 2FA: after signing in with your username and password you'll be prompted to confirm that it's really you signing in. You have to have an Internet-connected Android phone or an iOS device with a proper app installed. It works wonderfully but your phone needs to be connected to the Internet (and it works just for Google).
The Android built-in security key works in a similar fashion but doesn't even need the Internet. Google has yet to disclose any technical details but the whole thing works even if I tell my browser to stop using Web Authentication API via Bluetooth security keys. Maybe it uses the U2F API (based on the FIDO U2F API)? Seems so, FIDO is also mentioned in the page listing Google's security keys and Android 7+ is FIDO2 Certified since February.
Hopefully, the mobile security key is standards-based and will be available for other services, systems and apps. I really like that the industry is moving on and we're not stuck on entering digits that change every 30 seconds. The easier it is for people the more they'll be using it. And then of course, the threat of account takeovers will be much lower. Security keys are much more secure than a traditional SMS or copying codes as you can't enter them into a different page, they're phishing-resistant.
This is how you use it
If you want to set up the built-in security key you can follow Google's help or just look at my screenshots below.
In 2-step verification options, you can choose which “second step” you want to use when signing in. Security key is one of the options:
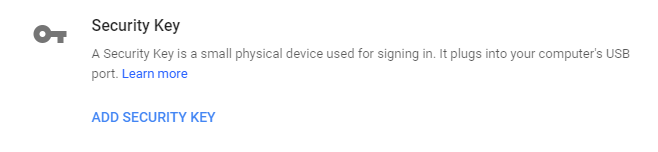
Don't be scared that it doesn't (yet?) mention Bluetooth devices
Then choose if you want to use an external USB or Bluetooth security key, or the one built into your phone that's signed in to your Google account:
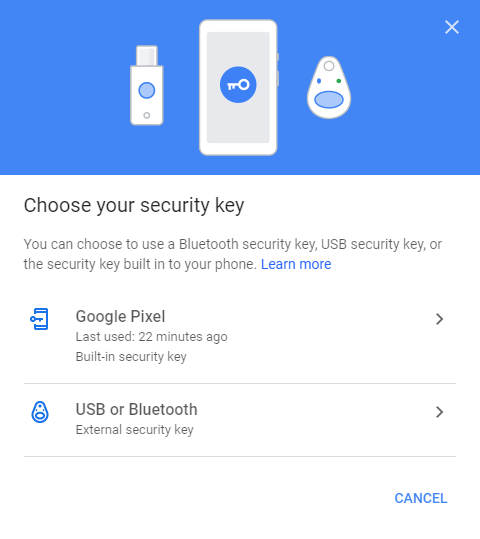
Choose the built-in option and then Google tells you both your phone and your computer need to have Bluetooth enabled, phone needs to have location enabled (and run Android 7 or newer) and that for now, it works only in Chrome (and also in Chromium-based browsers like Brave, Opera, or the new Edge):
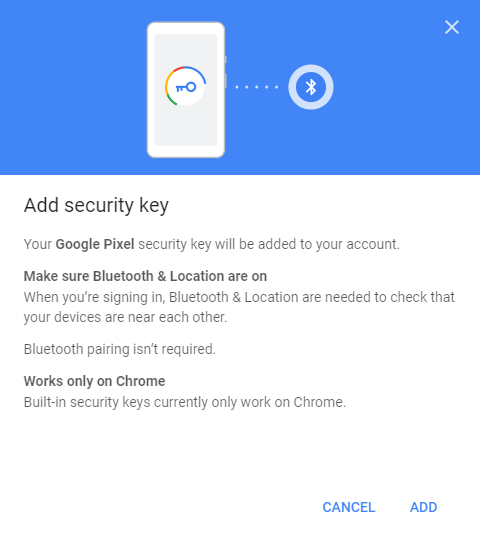
Hit “Add” and you're done. No Bluetooth device pairing, no codes to write down, no email confirmations:
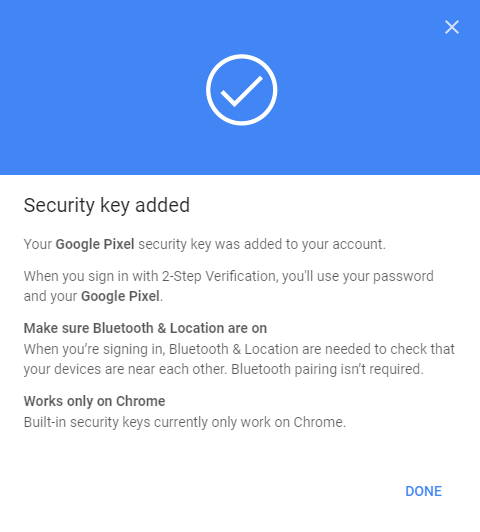
Once back in settings, you'll see your security key is the default confirmation option (I'd recommend to add at least one more alternative second step in case you loose your device for example) and that it's the built-in key:
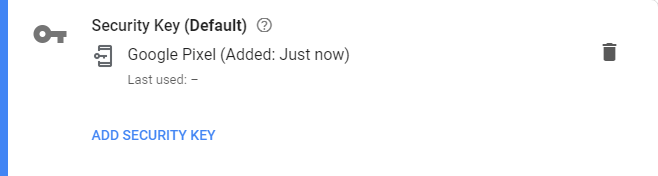
Signing in to Google
Once you enter your username and your password you'll be presented with a Chrome alert suggesting you check your phone. You can also use an external USB key if you have one:
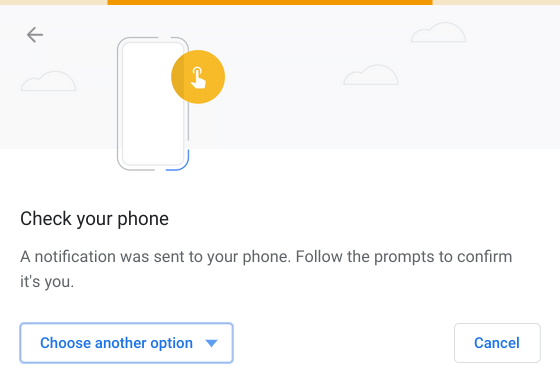
Once you unlock your phone you'll see a prompt asking you to confirm the login:
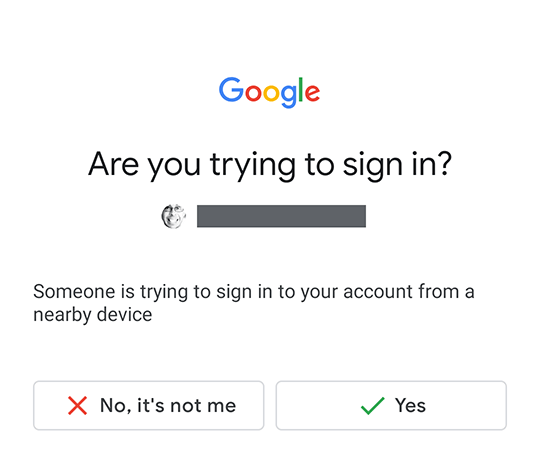
Select “Yes” and voilà, you're logged in. If you're signing in from a new device you'll probably see another prompt asking you to confirm the new device. Recently used devices page lists your known devices and you can remove the ones you don't use anymore. I'd recommend to check the list from time to time.
If your phone doesn't display the confirmation prompt for whatever reason, you can use an alternative second step which you've set up earlier.
Set up 2FA
I can't recommend setting up two-factor authentication (2FA, 2SV, the differences are irrelevant here) enough, even if you use a password manager (you do, right?) – like an extra layer of security. This built-in security key is a nice and highly usable option for anybody using Android 7 or newer, and I hope we'll see something similar elsewhere too. Google says you need Windows 10, Chrome OS or macOS X but I could get the “Check your phone” window on Ubuntu 18.04 as well. The phone didn't display the confirmation though but that might be due to the Ubuntu running in a virtual machine.
Also set up some alternative second steps in case your phone says bye. And don't forget to set this (or some other usable login confirmation option) up in your company, right after you give everyone a password manager.
And what about iOS?
Similar security key is available for iPhone and iPad since the beginning of 2019, thanks to the Google Smart Lock app. The app makes use of the Secure Enclave first introduced with the Apple A7 processor (iPhone 5S and newer). More information in Google's help.
Recommended reading
- A password manager can be a nice benefit not just for employees but also for the company itself
Updates
January 15, 2020 Security keys are now available on iPhones and iPads too
April 12, 2019 FIDO details and other Chromium-based browsers support
I build web applications and I'm into web application security. I like to speak about secure development. My mission is to teach web developers how to build secure and fast web applications and why.
Public trainings
Come to my public trainings, everybody's welcome:
