UR is a fast and secure web browser. With a built-in VPN, ad blocker, virus scanner and more, UR helps you protect your privacy online.
Except it doesn't. The “VPN” is just a proxy and the connection between the browser and the proxy server is not even encrypted.
UR browser is built by AdaptiveBee, and was launched in June 2016. In April 2017, while still in beta, it has been downloaded more than one million times. It boasts several Anti-Tracking and Anti-Profiling privacy features, one of them being a VPN, which hides your web traffic
and creates a secure “tunnel” for your data when you are online so that your data is encrypted and unreadable to anyone trying to spy on you.
At least that's what the site says. Having previously researched how Opera's “VPN” works this has caught my attention.
First things first, UR is based on Chromium 55, with Flash 24, as seen on chrome://version/:
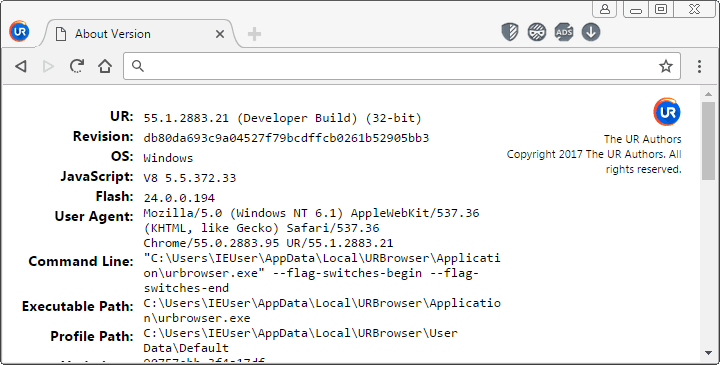
Current stable Chromium is 58 with Flash 25, new versions usually fix a handful of security bugs so you want to keep both updated. By using Chromium 55 released in December 2016 UR browser is failing at that. Their website also proudly says that nothing is reported back to Google
(except the files you download, see below) and lists Automatic updating as one of the disabled reporting features. On the other hand, privacy policy says that UR Browser periodically contacts ADAPTIVEBEE to perform functions such as checking for updates
. I'm a bit lost here.
Ninja mode (づ─⍘─)づ
The “VPN” can be enabled and controlled only from your Homescreen, or in an incognito window (called the Ninja mode), although when enabled, it works in regular windows too.
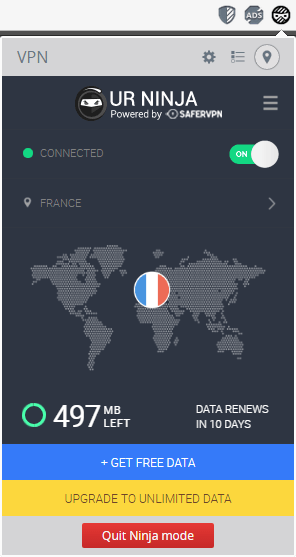
The “VPN” is powered by SaferVPN and initially offers 500 MB of of free “VPN” traffic each month. I use the term “VPN” because it's not a VPN, it's just a plain…
Unecrypted proxy
Update June 16, 2017: The “VPN”/unencrypted proxy is now completely removed in UR browser version 55.1.2883.54, good.
Update 2020: UR browser now offers a “common” VPN in cooperation with OVPN – at least that's what their privacy policy says, I couldn't verify as I got stuck on “Connecting”.
When you enable the “VPN” and check the Events or Proxy tab in chrome://net-internals, you'll see that the proxy configuration has changed:
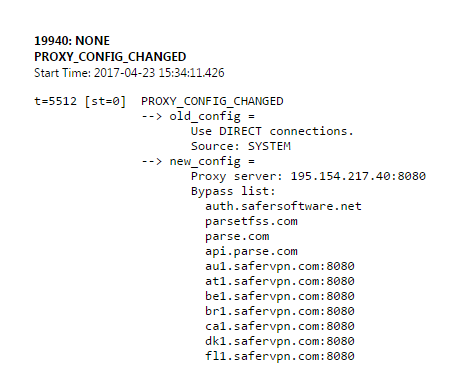
The proxy server is now set to one of the IPs used by SaferVPN, and the port 8080 suggests the connection to the proxy server is not encrypted. Now when loading a page the Events tab confirms the proxy server is used:
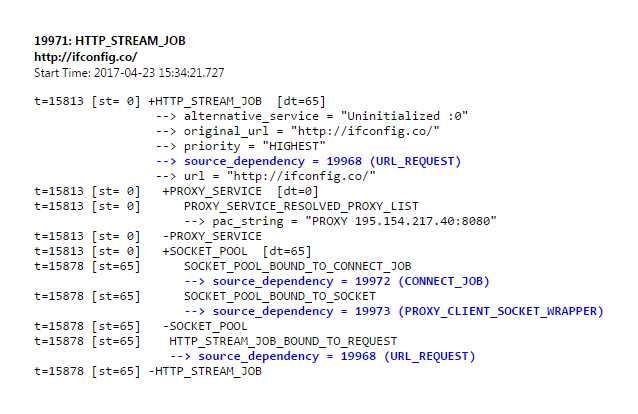
Let's focus on the proxy service log:
t=15813 [st= 0] +PROXY_SERVICE [dt=0]
t=15813 [st= 0] PROXY_SERVICE_RESOLVED_PROXY_LIST
--> pac_string = "PROXY 195.154.217.40:8080"
t=15813 [st= 0] -PROXY_SERVICE The string PROXY in the pac_string means regular proxy, while HTTPS would indicate encrypted secure proxy. Time to dump some packets I guess:
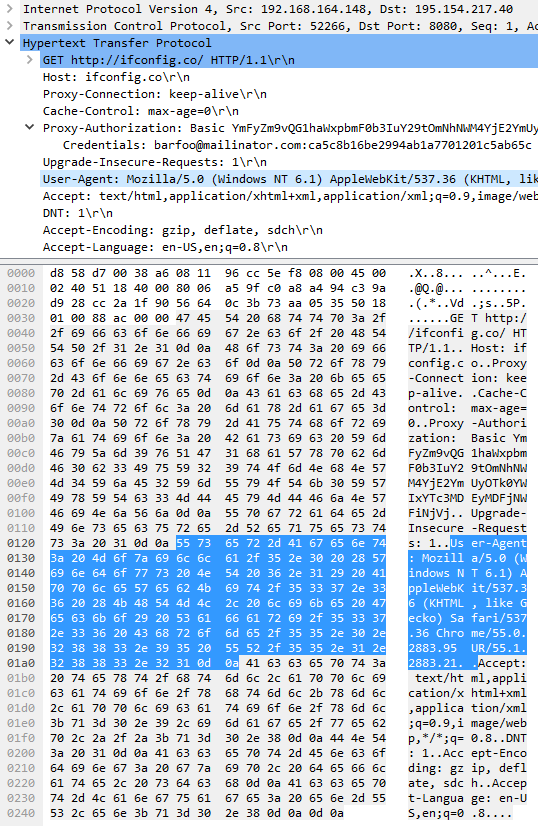
The connection between the UR browser and the proxy server is really unencrypted. Here you see the plain HTTP request GET http://ifconfig.co/ HTTP/1.1, the User-Agent header, and just about everything else being sent. Your data is not protected at all, despite the claim that your data is encrypted and unreadable to anyone trying to spy on you
. That's not correct, when using UR browser and its “VPN” feature your data is readily available to anyone listening.
Extension source
The “VPN” is implemented as an extension with id cmgcichealemeanengbbclalkbkdifcm, so it's possible to confirm the unencrypted proxy by reading the source code. The proxy is set in background.js, these are the important bits:
function setProxy(proxy, proxySetCallback) {
var proxyCfg = {
mode: "fixed_servers",
rules: {
singleProxy: { host: ip, port: port }
}
};
chrome.proxy.settings.set({ value: proxyCfg, scope: 'regular' }, proxySetCallback);
}According to chrome.proxy API documentation, if you don't specify scheme in singleProxy attribute, it defaults to unencrypted http. The fix is easy, the extension would need to add scheme: "https" to singleProxy. The proxies would need to speak TLS, which unfortunately doesn't seem to be the case. With scheme: "https" the connection between the browser and the proxy would be encrypted, just like what Opera does with their secure proxy.
Block ads with one click
The built-in ad blocker is just a rebranded version of Adblock Plus from August 2016 (extension id chboeokhjkjpnoklbbohmpfeecmdmkef), at least that's what info.js says:
addonName: "adblockpluschrome",
addonVersion: "1.12.2",Nothing is reported back to Google
UR browser comes with an integrated virus scanner
which verifies all your downloads
. Well, that's true only if you ever download files with these extensions: 7z, bat, cab, csv, cur, dll, doc, docx, exe, fla, font, gz, gzip, lz, lzip, msi, odp, pdf, pot, pps, ppt, pptm, pptx, pub, rar, rtf, tar, tar.bz2, tgz, ttf, txt, wps, xls, zip. Once again, the Downloader extension's virusScanner.js gave them away. So how does the scanner work? Every time you download one of those files, the browser will send it's SHA-256 hash to VirusTotal to see if it's a known malicious file. VirusTotal is owned by Google.
Worry not, all downloads (except filenames) are reported to core.beeapi.net, a service operated by AdaptiveBee, the makers of UR browser. This is a request triggered by me saving an image:
POST /v2/core?channel=BETA HTTP/1.1
Host: core.beeapi.net
Connection: keep-alive
Content-Length: 229
Content-Type: application/json
User-Agent: Mozilla/5.0 (Windows NT 6.1) AppleWebKit/537.36 (KHTML, like Gecko) Safari/537.36 Chrome/55.0.2883.95 UR/55.1.2883.21
Accept-Encoding: gzip, deflate, br
AppInstance-UID: 370aebe1-9b30-4f8f-932e-2de68136ee18
AppKey-UID: A5801B98-5507-4F71-8083-CCF835283A1F
{
"Action": "Download_File",
"AppInstanceUid": "370aebe1-9b30-4f8f-932e-2de68136ee18",
"AppKey": "A5801B98-5507-4F71-8083-CCF835283A1F",
"Category": "DOWNLOADER",
"CoreVersion": "55.1.2883.21",
"Label": "image/jpeg",
"OS": "win",
"OSVersion": 4
}Last but not least, the Homescreen is always loaded from http://hs.ur-results.com/, that's over plain HTTP, and it includes GPT, Google Publisher Tags, an ad tagging library.
★☆☆☆☆ wouldn't download again
The UR browser looks like a scam. Full of bold claims, but failing at most of them, not protecting users and their data. Avoid it.
Recommended reading
- Opera browser’s VPN is just a proxy, here’s how it works, with a comment from Opera
- The Oprah Proxy, generates credentials for Opera's “browser VPN”
Updates
June 1, 2020 The VPN feature now uses a common VPN, service offered in cooperation with OVPN
June 16, 2017 The “VPN” is now completely removed from the browser
I build web applications and I'm into web application security. I like to speak about secure development. My mission is to teach web developers how to build secure and fast web applications and why.
Public trainings
Come to my public trainings, everybody's welcome:
